
Pen testing guide Types, steps, methodologies and frameworks TechTarget - Earn a degree275+ university partnersflexible online learningfind a course It involves simulating cyberattacks to identify vulnerabilities and assess the effectiveness of. At the very least, there should be three phases: Read on to learn about what it takes to complete a successful pen test. This ensures the test is tailored to your unique environment and goals. You should also read this: Urinary Metanephrines Test
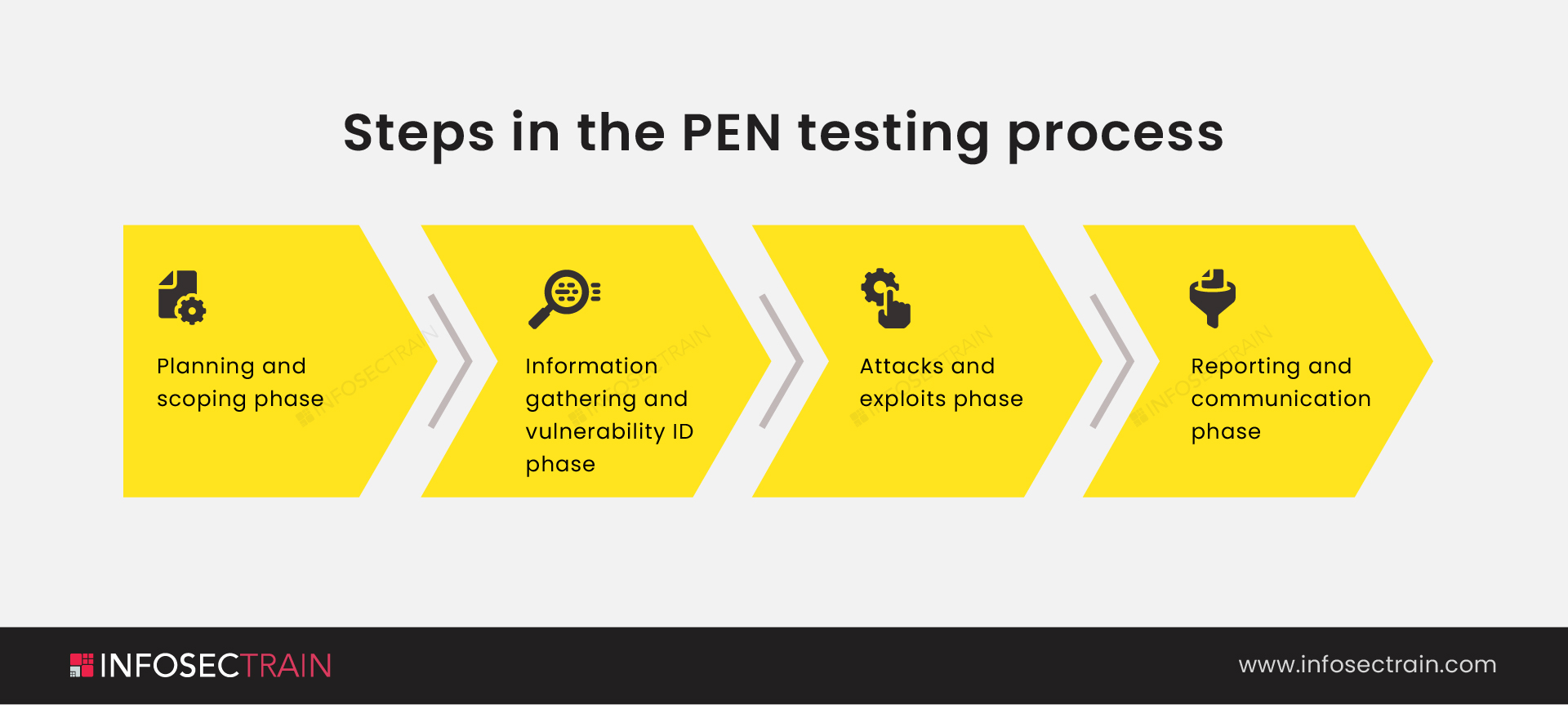
The Strategic Processes Behind Executing an Effective PEN Test - An overview of the main phases making up an effective penetration test. Defining the scope and goals of a test, including the systems to be addressed and the testing methods to be used. Gathering intelligence (e.g., network and domain names, mail server) to better understand how a target works and its potential vulnerabilities. It involves simulating cyberattacks to identify vulnerabilities. You should also read this: Quickvue Covid Test Expiration Date

5 Stages in a Test CyberQuote Pte Ltd Global - There are several different methods for penetration testing. What are the 4 phases of penetration testing? Penetration testing, or pen testing, is a simulated cyberattack on a system, network, or application to identify vulnerabilities that could be exploited by malicious actors. In this article, our team of ethical hackers discusses the responsibilities of a penetration tester and outlines the five. You should also read this: Spac 4 Grade Practice Test Math Ca
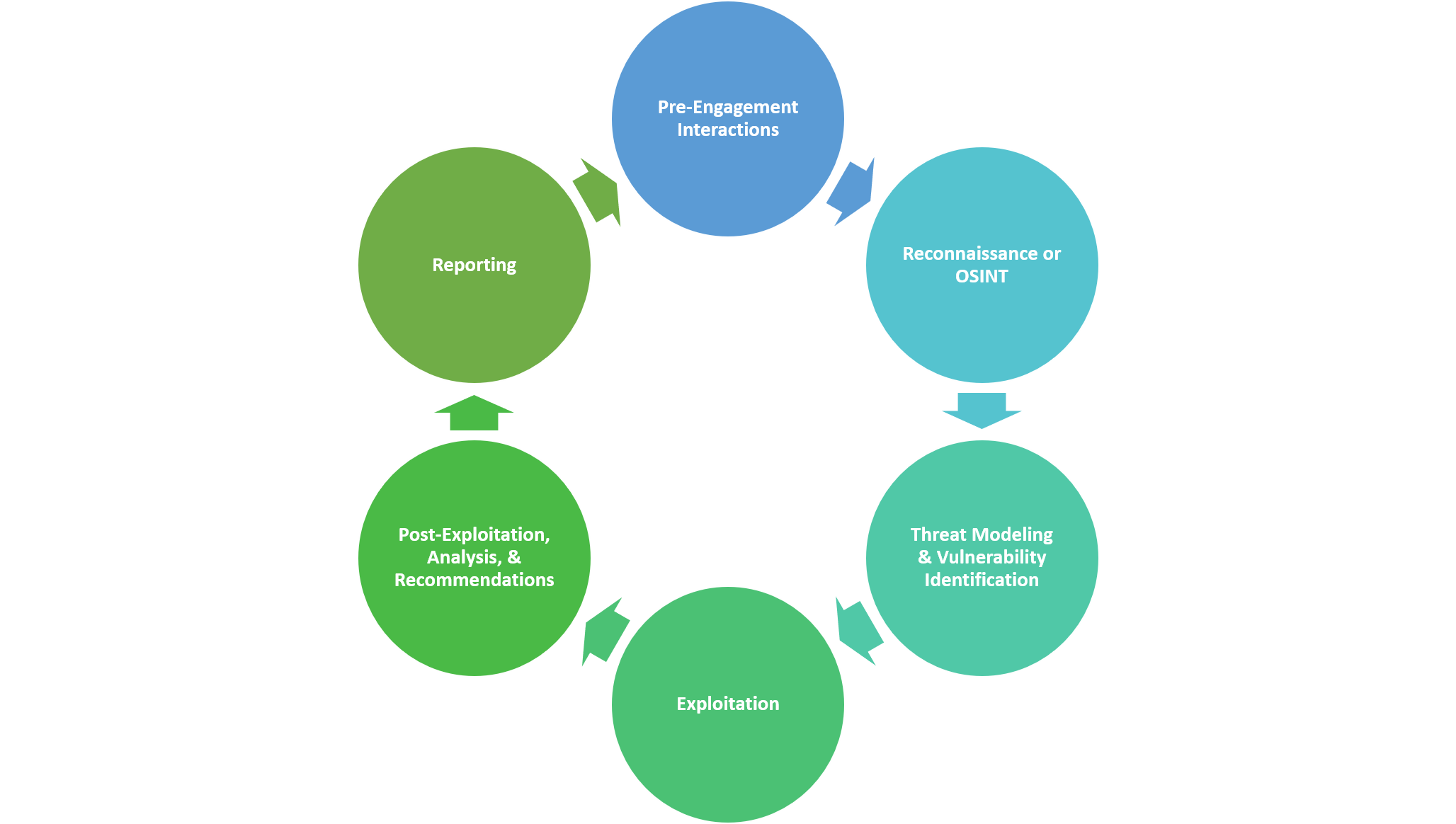
A Complete Guide to the Phases of Testing Cipher ES - Penetration testing is a structured process to identify and exploit vulnerabilities in systems, networks, and applications. It involves simulating cyberattacks to identify vulnerabilities and assess the effectiveness of. Read on to learn about what it takes to complete a successful pen test. Pen testing is often used interchangeably with ethical hacking, but these terms are slightly different. In this article,. You should also read this: What Is Cqa Test On Android
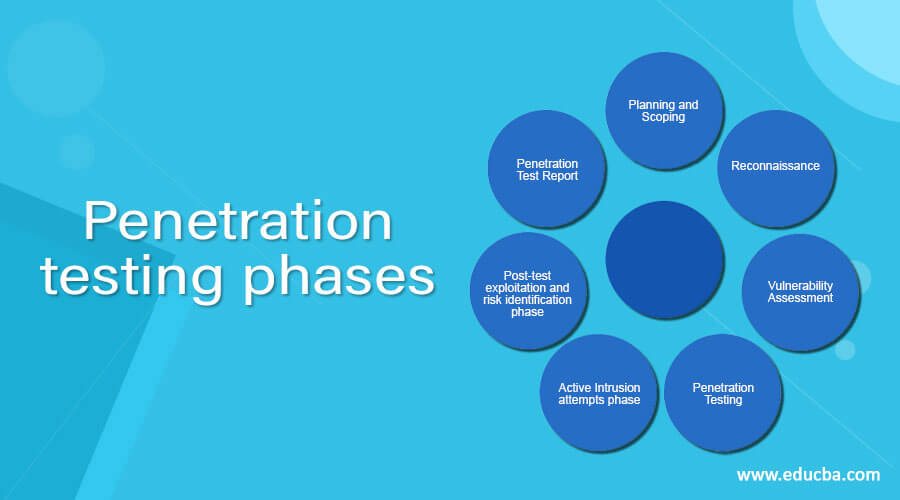
testing phases Learn the list of Phases of - What are the 4 phases of penetration testing? Each methodology, testing company, and standards organization often creates their own. Read on to learn about what it takes to complete a successful pen test. Defining the scope and goals of a test, including the systems to be addressed and the testing methods to be used. Pen testing can be divided into. You should also read this: Best Dpo To Take A Pregnancy Test

Phases and Steps of a Test — CyberSecurity Services - The pen testing process can be broken down into five stages. Read on to learn about what it takes to complete a successful pen test. It involves simulating cyberattacks to identify vulnerabilities and assess the effectiveness of. Here, we'll explain the pen testing process. Penetration testing is a structured process to identify and exploit vulnerabilities in systems, networks, and applications. You should also read this: Can Autozone Test Alternator Without Removing It
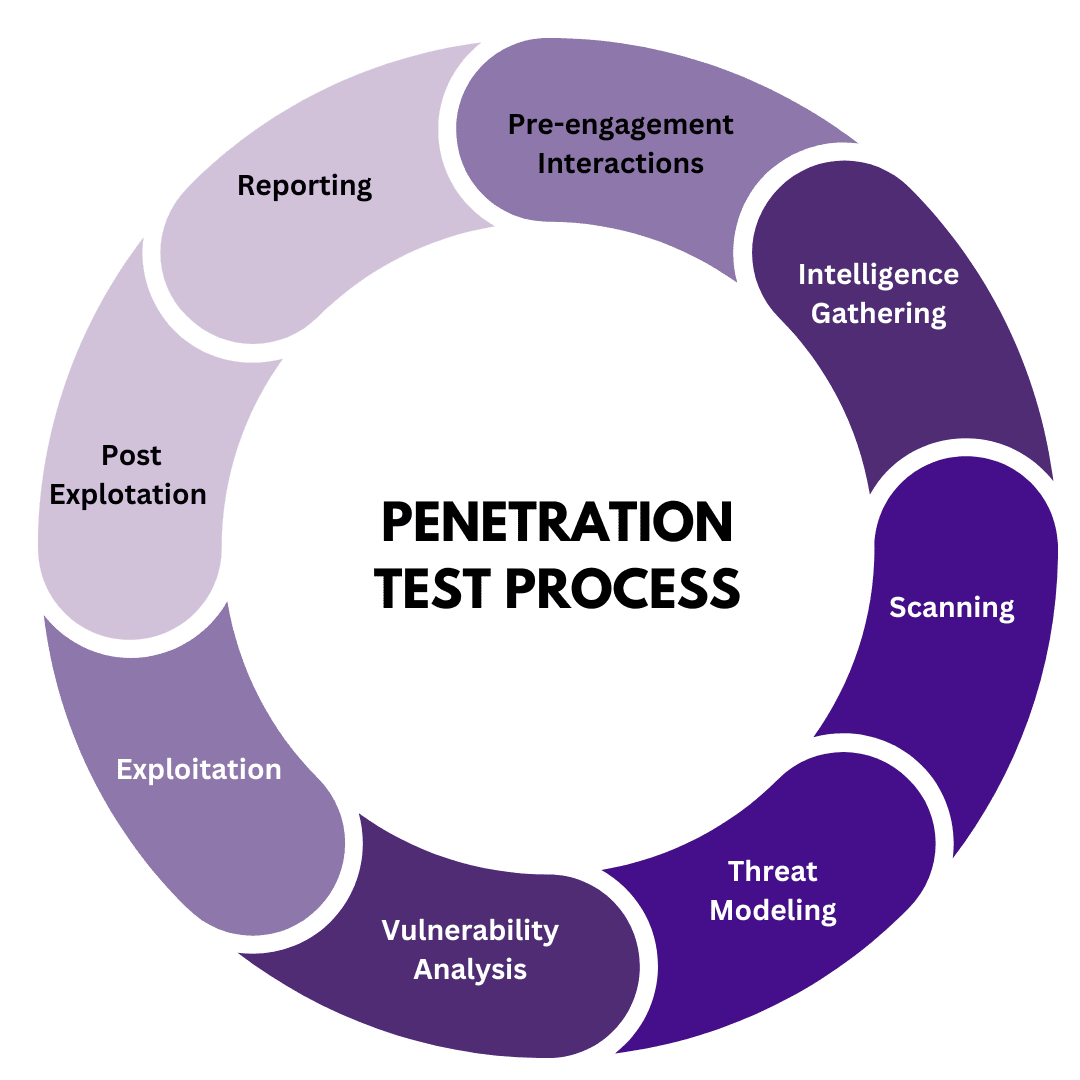
Testing Network Oppos Cybersecurity - From the initial reconnaissance phase, to scanning, vulnerability assessment, exploitation and the final. This ensures the test is tailored to your unique environment and goals. Pen testing can be divided into multiple phases that explain what is going on during the test. It involves simulating cyberattacks to identify vulnerabilities and assess the effectiveness of. Red teaming, penetration testing (pentesting), and. You should also read this: All Time Test Run Scorers
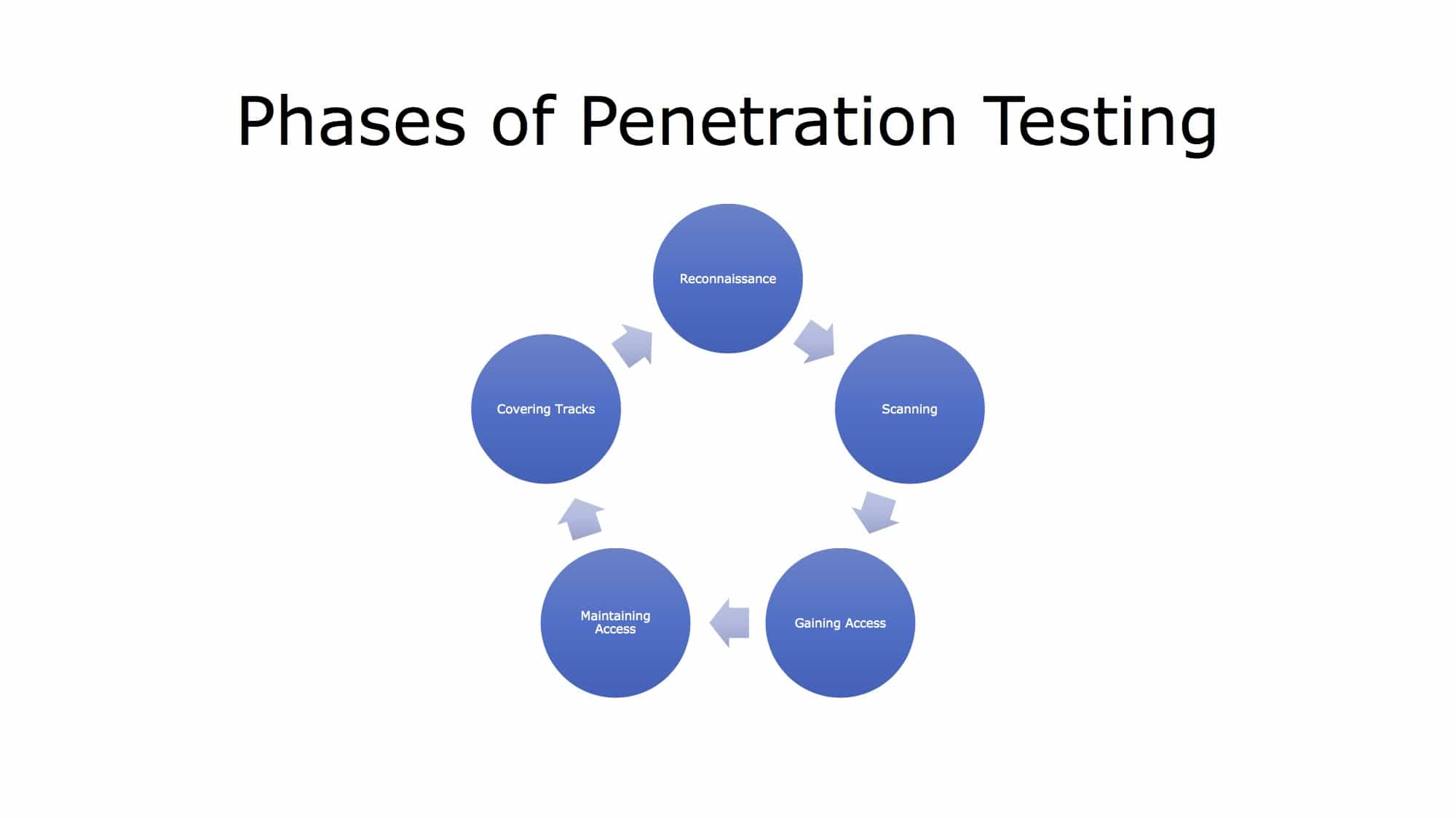
Module 11 Phases of Testing Gotowebsecurity - Red teaming, penetration testing (pentesting), and ptaas are often grouped together under the “offensive testing” label,. This ensures the test is tailored to your unique environment and goals. Pen testing is often used interchangeably with ethical hacking, but these terms are slightly different. Read on to learn about what it takes to complete a successful pen test. The pen testing. You should also read this: Ap Human Geo Unit 4 Practice Test

Five Stages Process Of Testing PowerPoint Templates - Each methodology, testing company, and standards organization often creates their own. Defining the scope and goals of a test, including the systems to be addressed and the testing methods to be used. According to ibm’s cost of a data breach report, unpatched vulnerabilities, stolen credentials, and system errors can cost enterprises anywhere from $4m to $5m in damages. 210,000+ online. You should also read this: Neurofilament Light Chain Blood Test For Ms
10 Best Testing Phases & Life cycle 2023 Guide - The pen testing process can be broken down into five stages. Gathering intelligence (e.g., network and domain names, mail server) to better understand how a target works and its potential vulnerabilities. Penetration testing, or pen testing, is a simulated cyberattack on a system, network, or application to identify vulnerabilities that could be exploited by malicious actors. A phased approach to. You should also read this: Jpg Ultra Male Tester